Hi all,
This story happened last year, and I thought it would make a good case study on taking advantage of broken links. Additionally, it includes a funny story that shows how I find security issues wherever I go.
Introduction
Last year, I traveled to Dubai to explore the city and meet some good friends: Yasser, Ahmed, and Ayoub.
I am a loyal user of Careem; I use it most of the time wherever I travel, including in Iraq. When it was time to travel back home, I ordered a taxi via the Careem app. I waited, and the driver was somewhere nearby my hotel. I took my bag and waited on the sidewalk, hoping he would see me since it was early morning and nobody else was around. He saw me but never moved. I was waving at him, but he left and canceled the ride, marking that I didn’t show up.
I was frustrated and ordered another ride since I needed to get to the airport as soon as possible. The new driver was nearby, so it didn’t take much time. However, I found that the Careem app had already charged a fee for the previous ride that I didn’t take!
When I returned home, I wrote a complaint about the trip. They called me, and I explained what happened. They apologized and refunded the ride fee. Heeey!
Technical Details
After a while, I received an email from their Customer Care asking if I was satisfied with my last interaction with their team. There was a broken link in the email, and I was perplexed as to why they hadn’t noticed it.
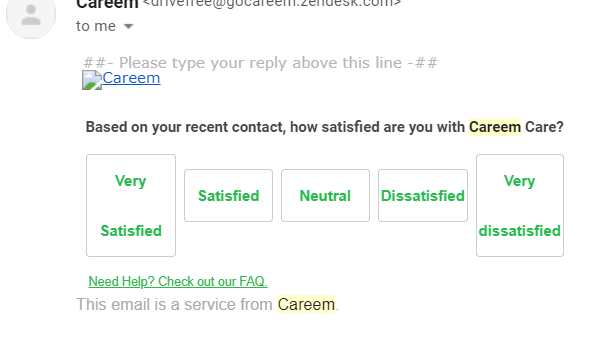
I used the inspect element tool in the browser to look at the broken link. The link was:
<img alt="Careem" title="Careem" src="https://ci5.googleusercontent.com/proxy/VFkr93bHbGyGsKAShSjEy1Wa5c2_E1roaPHqkXAgvfFVAe-4cPZ59CKXCpY-vig5E96sY7ojsvKFiy8uAkfA564sndlRHO01J_LqgsbCJyyzudeSS78=s0-d-e1-ft#https://s3.amazonaws.com/careemcrm/promotional/careem_logo_Care.png" class="CToWUd">
Since I was using Gmail, there is a feature that prevents photos from being viewed directly. So, the real link of the image is the one after the location hash, which is:
https://s3.amazonaws.com/careemcrm/promotional/careem_logo_Care.png
I thought that the careem_logo_Care.png was deleted, causing the error. I checked the bucket link and it showed the following response:
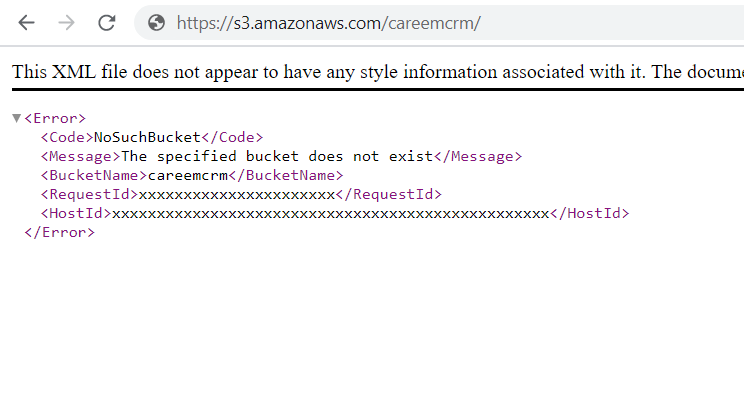
As you can see, the response says XYZ, which in the security world means that we can take over this bucket. That’s what happened. I used the AWS CLI with my AWS account to register the bucket. Then, I copied a file from my PC to the S3 bucket.
And here is our PoC:
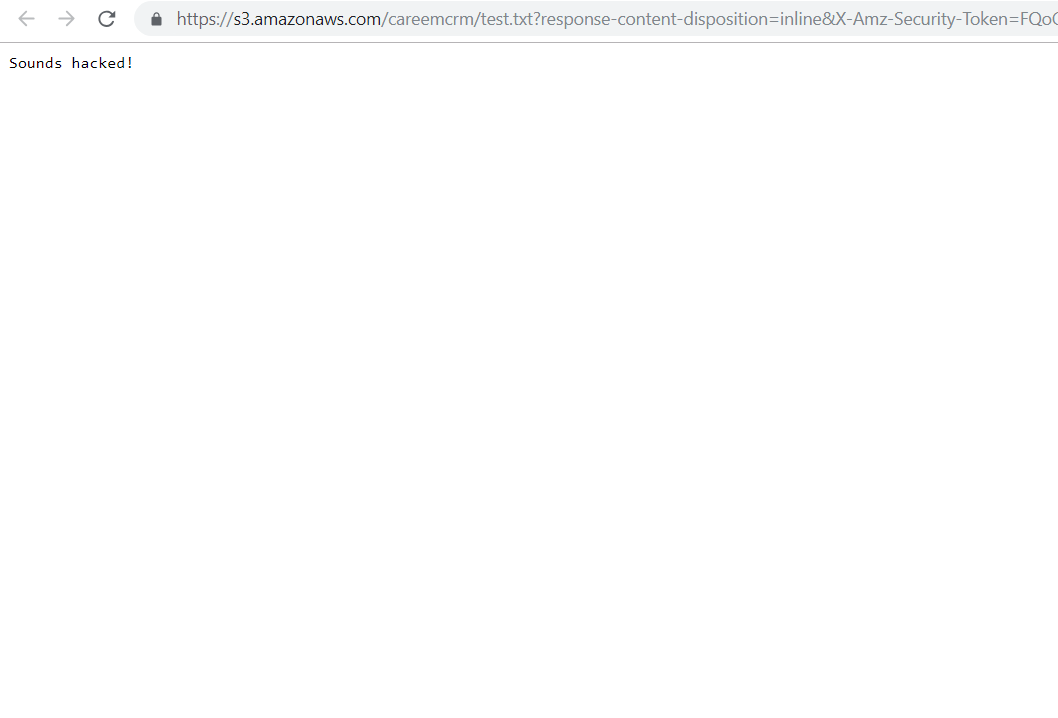
I tried to find where I could report this issue but to no avail. Careem has no bug bounty program, so I was a little disappointed that such a reputable company lacks one.
I contacted a friend who works at the Careem office in Iraq. He forwarded me to the security team, and they fixed the issue. I told them I would remove the S3 bucket from my account so they could reclaim it, but they said they didn’t want it anymore.
They emailed to inform me that they fixed the issue. The root cause was:
Based on your initial description and proof-of-concept, this appears to be an abandoned S3 bucket that may belong to someone who used to work with the company. As a result, no one handed over all the necessary information.
For Bug Bounty Hunters & Security Engineers
Importantly, make sure to keep an eye on broken links and links in emails, PDFs, or for old events.
URL Tracker Project!
I created a side project to help track all cloud services and links that may open the door to takeover issues. The project is still in progress, and you can follow it here.
What now?
If you think your site/app/network is secure and want to ensure it, then give us a call at contact@cube01.io.