Last year, I got an invitation from a private bug bounty program on HackerOne platform. I said let’s give it a try since I had some free time and here is the story of how I take advantage of an out-of-scope domain to earn $1250 bounty.
Introduction
Note: in this text out-of-scope refers to out of scope domains, not bugs.
First, as we all know out-of-scope is a bug bounty rule that you need to respect for multiple reasons including, but not limited to:
- The team know that there are vulnerabilities in these domains and working on solving them before they include it in the scope.
- The BBP has a small budget to cover these domains.
- These domains are for users only, and any interaction with users that can cause a damage is unwanted.
Although, you can use these domains to cause a harmful attack on the in-scope domains. We saw a lot of examples in bug bounty programs where the escalation had been done using an out-of-scope domain. Additionally, an RCE on an out-of-scope domain may be counted as a valid report like mail.ru bbp.
So, I was doing the recon when I found a subdomain that was using AnswerHub, meanwhile, I had a bug to create a stored XSS in that system. However, I won’t get into details because I have explained it in my previous write-ups, you can check them out: How I Hacked [Oculus] OAuth +Ebay +IBM, Leaking Amazon.com CSRF Tokens Using Service Worker API. Also, these two write-ups are good examples of escalation and out-of-scope domains use.
Technical Details
first of all, I read the bug bounty rules of the program, it is very important to read the whole page don’t forget any details that may be used against you or you will be disqualified.
After I found the subdomain list using sublist3r I found this subdomain answers.target.com which was using AnswerHub and was affected by the previously mentioned vulnerability. Unfortunately, I didn’t find it inside the in-scope domains. So I didn’t submit a report for the team and said let’s look further and I will ask them if they are interested in this issue when I submit a report in the future.
I start looking for bugs in in-scope domains. I was checking an Angular app that was hosted on developer.market.target.com I checked some angular and JS tricks. I found something while typing in the console I was on developer.market.target.com and I typed:
>>document.domain
>>"target.com"In the meantime I knew I found a bug here, so I checked the source code of the page and found this line in the head script on developer.market.target.com:
document.domain = "target.com";Let me explain why this is a dangerous issue that can be used to bypass SOP. You can make two pages from a different origin to interact with each other if they are sharing the same second-level domain, in our case the developer.market.target.com set the document.domain property to target.com so if we set the document.domain property of answers.target.com to target.com, we can create a frame for developer.market.target.com and execute code on the developer’s site. Here is a live version of the trick:
http://sandbox.ahussam.me/pocs/same-parent.html
As you can see I read the secret paragraph from a cross-domain.
One more thing we need to frame the page of developer.market.target.com, but the x-frame-option header was set to Deny :(.
I went to sleep and in the next day, I found that the /support/ path has no x-frame-option header which we can frame :D.
For simple PoC I wrote the following script saved it as poc.xml and uploaded to answers.target.com.
<?xml version="1.0" encoding="UTF-8"?>
<!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Strict//EN"
"http://www.w3.org/TR/xhtml1/DTD/xhtml1-strict.dtd">
<html xmlns="http://www.w3.org/1999/xhtml">
<head>
<title>PoC</title>
<script type="text/javascript">
document.domain = 'target.com';
function exploit(){
var i = document.getElementById("my_frame");
var exp = i.contentWindow.document.getElementsByClassName('ng-binding')[3].innerText;
alert(exp);
}
</script>
</head>
<iframe src="https://developer.market.target.com/support/" id="my_frame" onload="exploit();"></iframe>
</body>
</html>I checked the PoC and everything worked well. I was able to read data and execute JS on developer.market.target.com which is in the scope :D
Steps To Reproduce:
- Go to
https://answers.target.com, open any question and click reply. - Upload this file poc.txt as an attachment and intercept the request.
- Change
Content-Typefromtext/plaintotext/xmland forward the request. - Go to the attachment URL, you will access the contentWindow of developer.market.target.com and you will see an alert box that contains your username.
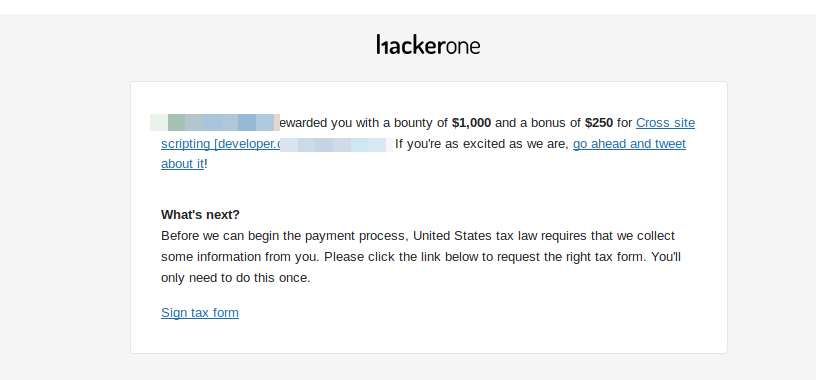
I reported the bug to the program and they were very fast and I got $1250 for an XSS!
Remediation
They fixed the x-frame-option header with CSP, and the AnswerHub issue too now my XML file is being served as a text file.
Conclusion
In brief, you may be able to escalate your attacks by using API’s, JS workarounds, a misconfiguration on a domain that isn’t under the program scope.
I hope you enjoyed reading the write-up and learned something.
If you like it feel free to retweet it :) and follow me on twitter@Abdulahhusam.