Early in 2015, while exploring bug bounty programs, I discovered that Oculus was within the scope of Facebook’s bug bounty program.
When a product is in scope, a bug bounty hunter should investigate all subdomains and main domains. At that time, the domain for Oculus was https://developer.oculusvr.com.
I noticed a menu link to https://answers.oculus.com. After browsing, I found that you could upload images in the comments, which intrigued me.
How does it work?
When you upload an image in the comments, the first filter checks if the uploaded file is an image by verifying if the name ends with an image extension.
The request includes image=true.
I uploaded a file named “xxml.jpg” and used Burp Suite to intercept the request, changing the content type to text/xml, then forwarded the request.
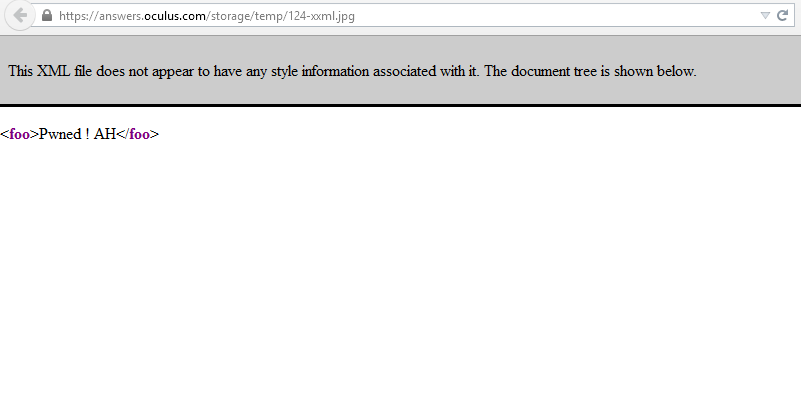
Next, I uploaded an XML file. Attempts with .php and .html resulted in a 500 server error. Seeking a more impactful attack, I used a SWF file. SWF files can be used for SOP bypass, XSS, open redirects, and leaking CSRF tokens because they are stored in cookies. There is a useful tool by @evilcos called xss.swf, available here.
Now, let’s try with .swf:
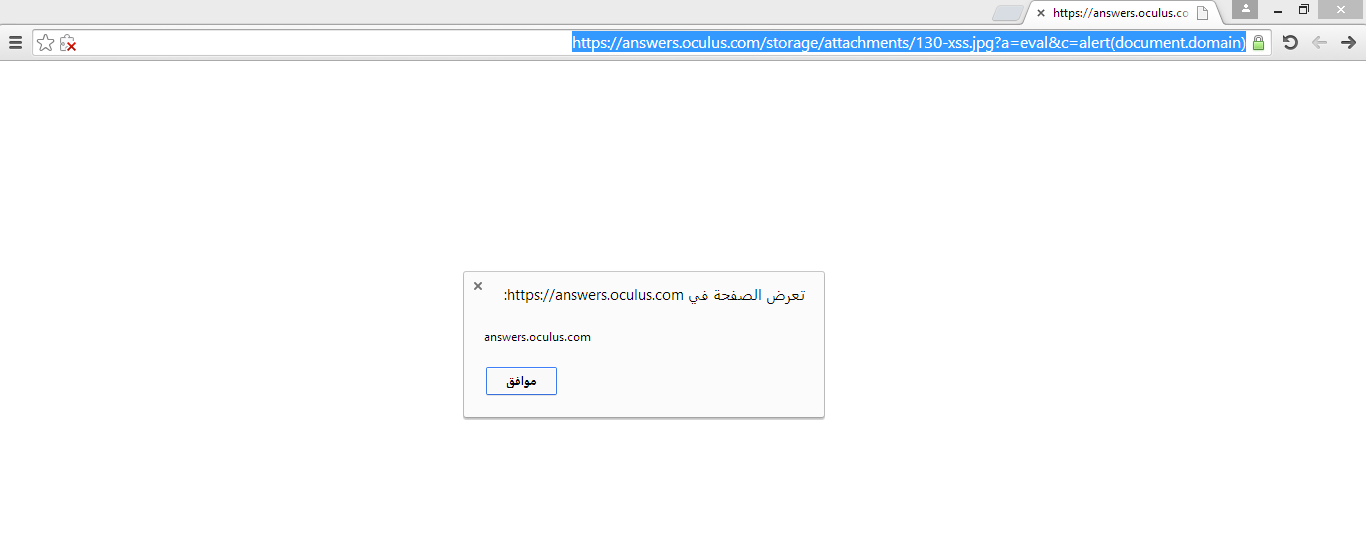
I intercepted the request, changed the content type to application/x-shockwave-flash, and forwarded it. Here is a video of the process:
I uploaded an evil SWF file.
Everything was set, so I reported it to Facebook.
After a while, Facebook closed my account and replied:
Hi Abdullah, Thank you for your report. This subdomain is actually not part of the Facebook bug bounty program and is hosted by AnswerHub. If you believe you have discovered a security vulnerability in that site, please consider responsibly disclosing it directly to them. Thanks, Mark Security Facebook
I was disappointed as I thought every domain *.oculus.com was in scope. I logged in using api.oculus.com, hoping to steal an access token. After some research, I found I could steal the token using the uploaded SWF file.
The final URL PoC was:
https://api.oculus.com/v1/oauth2/authorize?client_id=answerHub&response_type=token%20id_token&nonce=-blahblah&state=&redirect_uri=https://answers.oculus.com/storage/attachments/131-xss.jpg&country=US&locale=en_US
Due to improper validation of redirect_uri on api.oculus.com, I could change its value, allowing for open redirects, affecting api.oculus.com, which was in scope.
I reported it again:
Hi Mark, I know it is hosted on AnswerHub, and I will report it to them, but answers.oculus.com can be used to steal access tokens from api.oculus.com, affecting (api.oculus.com), which is in scope. It can also be used for redirects. Logged out and open this URL, you will see the login page, and when the user logs in, they are redirected to the SWF file that steals the access token, affecting Oculus OAuth. URL://URL
Open redirect example:
URL://URL
This should be a bug in the Oculus system.Thanks.
I received the following reply:
Hi Abdullah, Thanks again for writing in. The improper validation of
redirect_urionapi.oculus.comwas already known to us due to a previous report. A fix is currently being tested. As Mark mentioned, sinceanswers.oculus.comis hosted by a third-party called AnswerHub, the stored XSS issue on AnswerHub is unfortunately out-of-scope. I encourage you to reach out to them directly and inform them about the issue. Thanks, Aaron
Security
Since it’s a third-party service, other companies use it too. I created a Google dork to search for it and got good results like eBay, IBM, and more!
I repeated the process for each site, and here are the results:
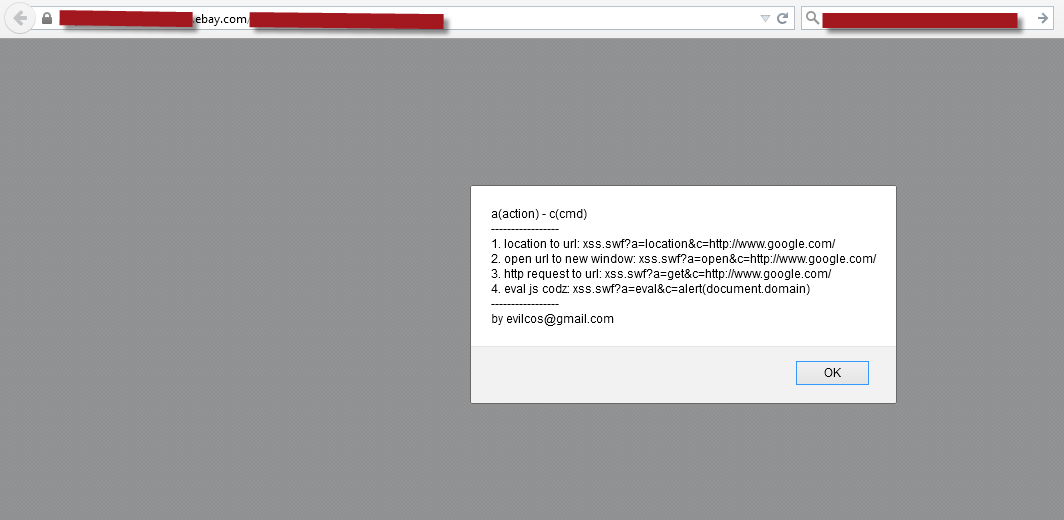
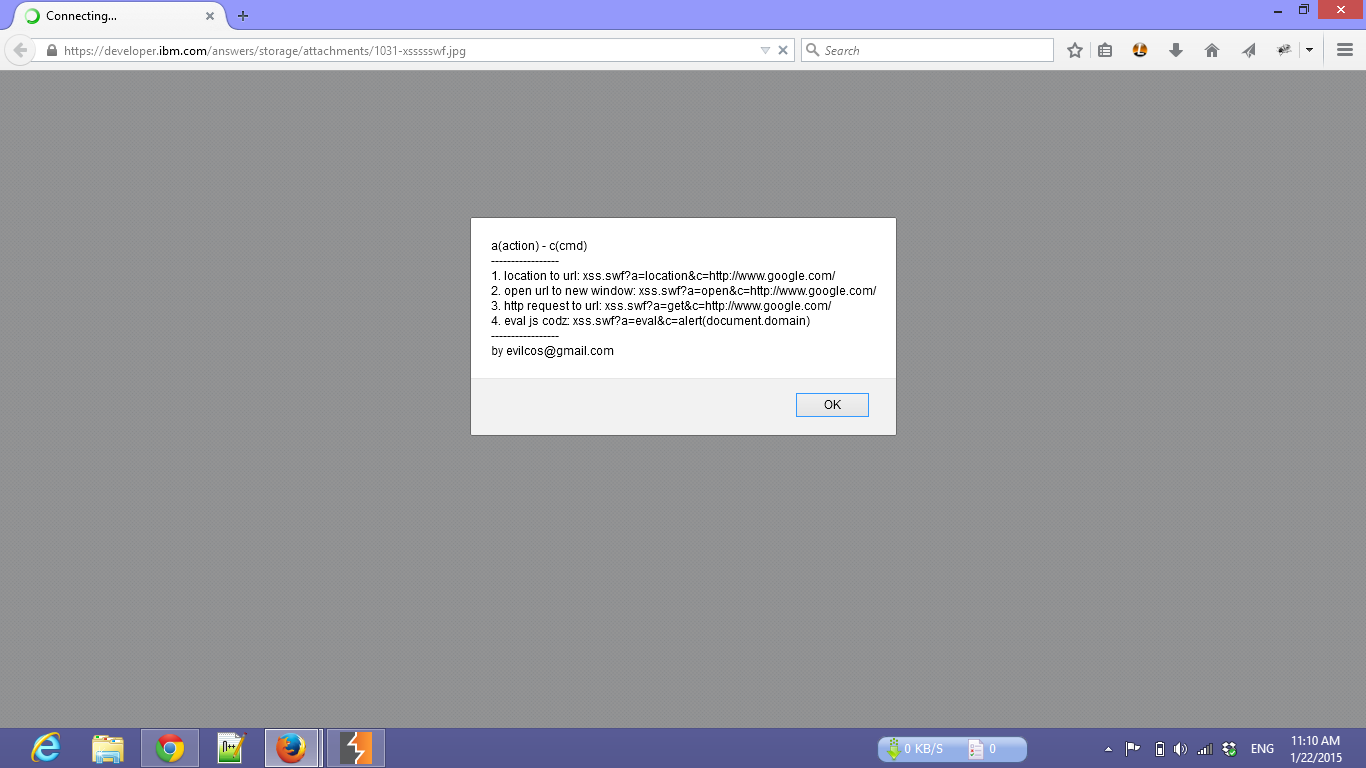
I then reported it to AnswerHub by contacting Matthew Schmidt, the CTO of Dzone, the builder of AnswerHub, a paid service. They did not offer a bounty but promised to send a package of Dzone items, which I never received. Weeks later, they published a release note without my name, so I contacted them again, and they added my name, though they misspelled my last name. Here’s the link: http://answerhub.com/releases/changelogs/answerhub-1.6.3-release-change-log/
I informed Facebook about all this, and Neal Poole replied:
Hi Abdullah, Glad to hear it! Thanks, Neal
Security
That’s all! Thank you for reading. You can contact me on Twitter @Abdulahhusam.
Take care.