One Payload to XSS Them All!
Introduction
Today, I want to share one of my findings from 2013—an XSS vulnerability in a widely used Flash file. The affected file, called sIFR (Scalable Inman Flash Replacement), was utilized by numerous high-profile websites, making it a significant security issue.
How Did I Find It?
Until recently, I believed I was the first to report this issue. However, upon further research, I discovered that this vulnerability had already been assigned a CVE. Nonetheless, my findings confirmed that the vulnerability still existed and was actively exploitable across multiple domains.
While hunting for a vulnerability in Adobe, my browser directed me to the following URL:
http://wwwimages.adobe.com/www.adobe.com/lib/com.adobe/sIFR2.0.2/myriad.swf?txt=ADOBE%20PHOTOSHOP%20CS3&textcolor=
At first glance, the txt parameter contained simple text, while the textcolor parameter accepted HTML color codes. Curious about its flexibility, I modified the txt parameter by injecting XSS instead of ADOBE PHOTOSHOP CS3.
Payload Test:
http://wwwimages.adobe.com/www.adobe.com/lib/com.adobe/sIFR2.0.2/myriad.swf?txt=<a href="javascript:alert('Xssed by Abdullah')">xss</a>
It worked! The page executed my JavaScript payload.
Refining the Attack
I noticed something intriguing in the URL—it resembled a file path within www.adobe.com. To test this, I removed wwwimages.adobe.com/ from the URL and navigated to:
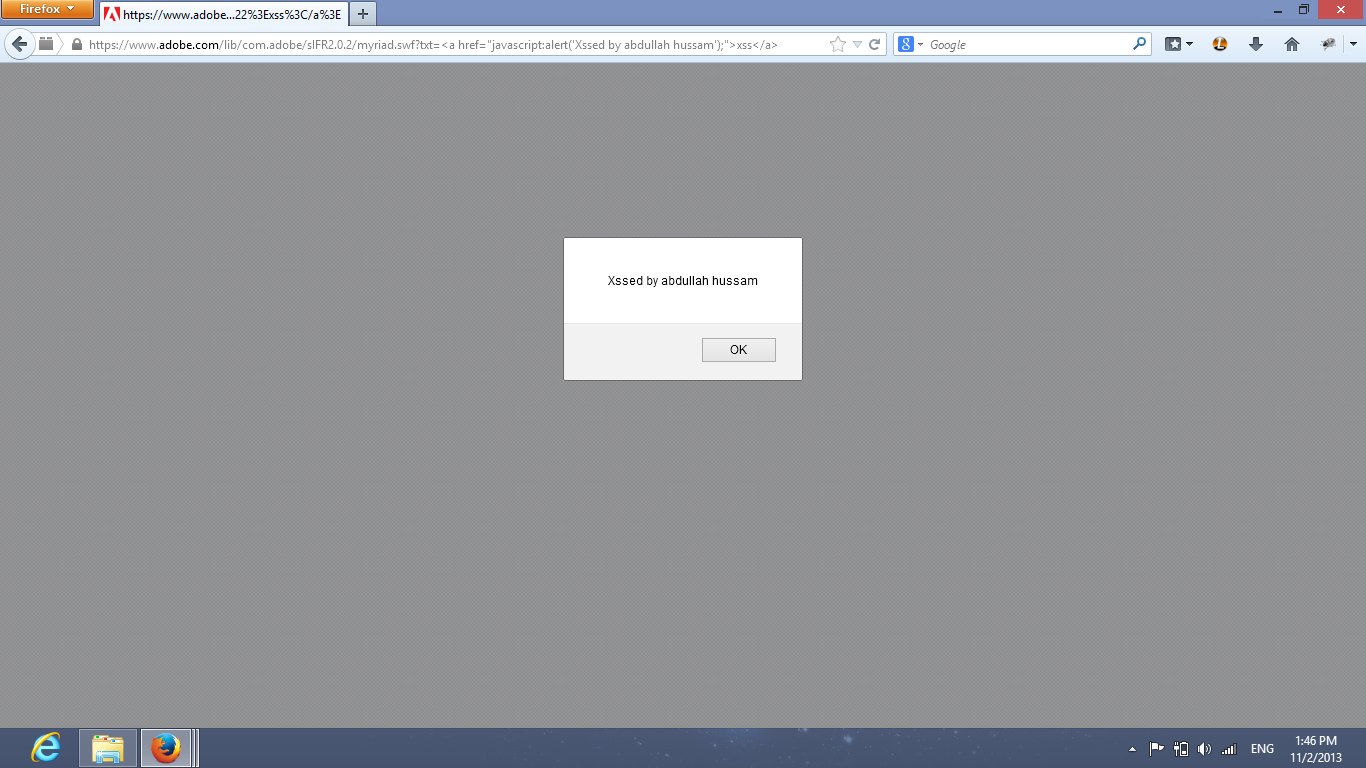
https://www.adobe.com/lib/com.adobe/sIFR2.0.2/myriad.swf?txt=<a href="javascript:alert('Xssed by Abdullah')">xss</a>
The exploit remained functional, demonstrating that the vulnerability existed on the core Adobe domain as well.
Proof of Concept
This marked the beginning of my bug bounty journey, and I was thrilled to find such an impactful vulnerability early on. But my research didn’t stop there.
Expanding the Search
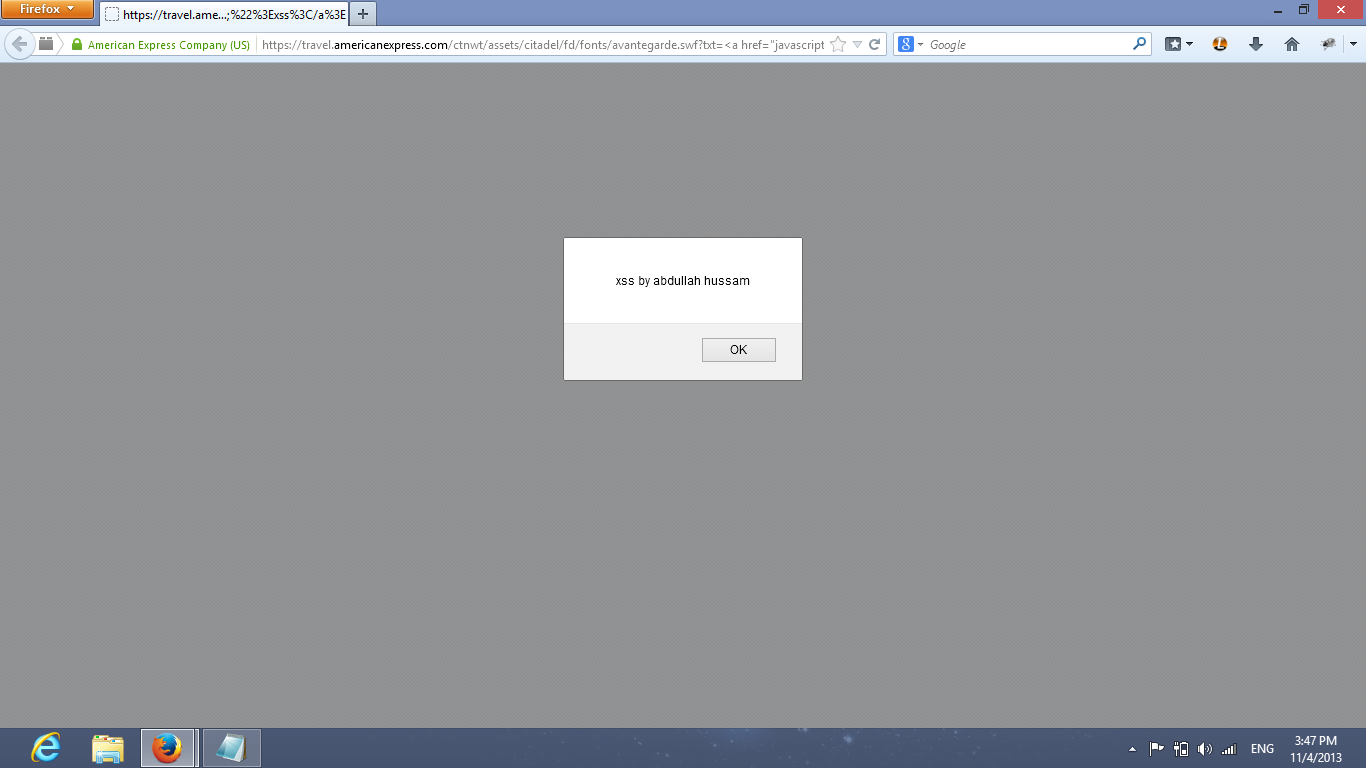
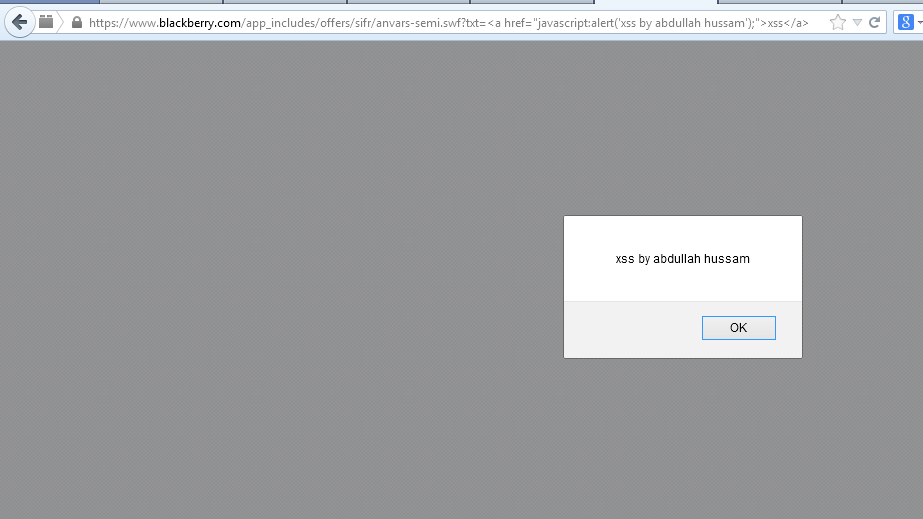
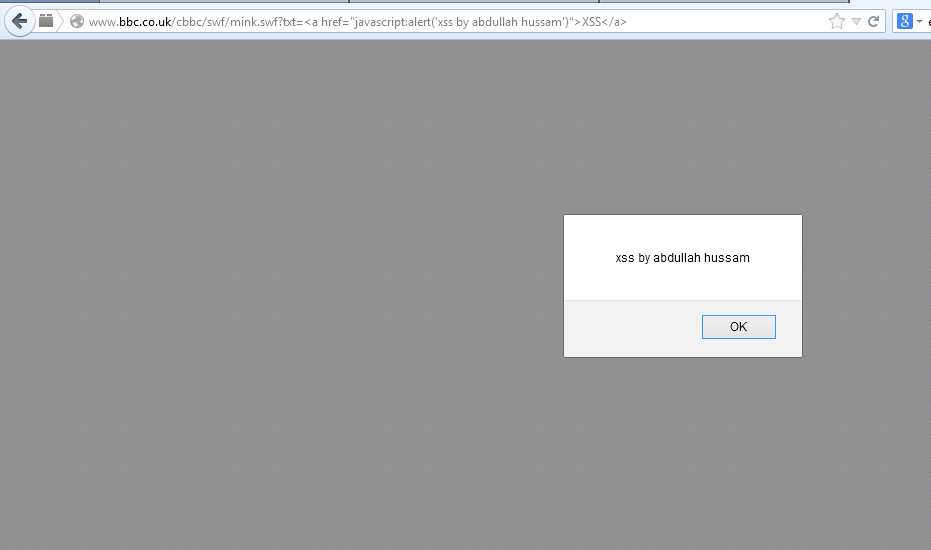
Realizing that sIFR 2.0.2 was likely not exclusive to Adobe, I started searching for other websites using the same Flash file. To my surprise, I found it deployed on websites belonging to major corporations and government organizations, including:
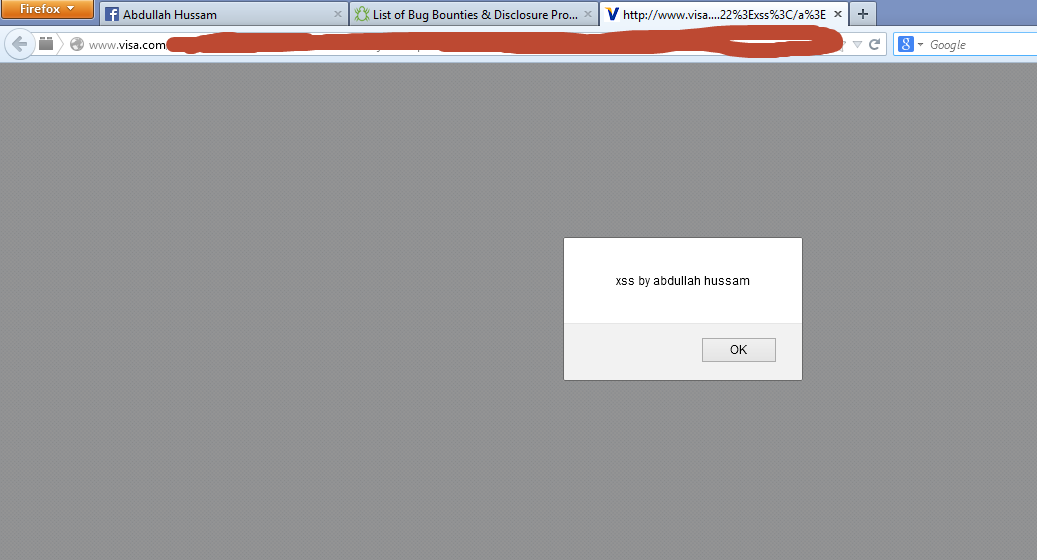
- Visa
- American Express (AMEX)
- Blackberry
- Stanford University
- Harvard University
- BBC
Real-World Examples:
PoC Video
For a live demonstration of the exploit, watch the following video:
Conclusion
This vulnerability demonstrated the widespread risks of outdated Flash files containing security flaws. Even though sIFR was a well-known vulnerability, many high-profile websites continued using it, leaving them exposed to XSS attacks.
Key takeaways:
- Always sanitize input parameters, even in third-party scripts.
- Regularly audit and deprecate outdated technologies like Flash.
- Even old vulnerabilities can remain exploitable for years.
There are still many other websites that remain vulnerable to this issue, making it an ongoing security risk.
Thank you for reading!